2013-02-03
2013: We Survived the Myans
BuggStompers 2013.
New names, new faces, new mission.
From now on, BuggStompers will be posting a new article every Sunday, with extras tossed in as something interesting comes up. New virus warnings, security threats, solutions, tips, tricks, reviews; this blog will be your one stop source.
And now for something completely different.
A suicide bomber was taken out early when her phone set off a bomb, sent by a spambot, saving countless lives. Irony at its finest.
2010-01-04
Backpedal! Backpedal!
So, your computer just crashed and you've lost everything. Well, I'm sure you've learned your lesson and will back up your important data, right? It can be a hassle, though, to carry a thumb drive, portable hard drive or (Cthulu forbid!) floppy disk with you. You might lose it, it might be stolen, eaten by your dog, used for a school project by one of your kids or abducted by aliens. Whatever the cause, you can (and will) lose whatever you're backing up on.
Is there a way to prevent this, you ask?
Yes, there is.
When I had lost my 20th thumb drive, I just started sending myself files in mail. I got a nifty little online email address and just sent the file I needed to myself. The internet had become my portable drive.
The process is simple. Get yourself a web-based email, such as Gmail (or Yahoo), and log in. Compose a new note and make yourself the recipient. In Gmail, under the Subject bar, look for the 'Attach a file' button. Browse to where you file is. Click on it and wait til it is loaded. Then hit Send. Google now has your file stored away, safe and sound.
You can now log into your email address from any Internet connected machine in the world and you can access that file. Gmail is now your own personal back up device, averaging about 7400 MB. That is over 7 Gigabytes of data storage space, free. Safe, secure and you can never lose it.
Unless you forget what your password is. But that is another article.
Is there a way to prevent this, you ask?
Yes, there is.
When I had lost my 20th thumb drive, I just started sending myself files in mail. I got a nifty little online email address and just sent the file I needed to myself. The internet had become my portable drive.
The process is simple. Get yourself a web-based email, such as Gmail (or Yahoo), and log in. Compose a new note and make yourself the recipient. In Gmail, under the Subject bar, look for the 'Attach a file' button. Browse to where you file is. Click on it and wait til it is loaded. Then hit Send. Google now has your file stored away, safe and sound.
You can now log into your email address from any Internet connected machine in the world and you can access that file. Gmail is now your own personal back up device, averaging about 7400 MB. That is over 7 Gigabytes of data storage space, free. Safe, secure and you can never lose it.
Unless you forget what your password is. But that is another article.
2008-06-09
Spring Cleaning
Time for spring cleaning.
While summer is still a couple of weeks away, now is a good time to pay attention to your computer and its needs for the long hot days ahead. Many people fail to realize that their computers need a good cleaning every now and then. Some people assume that I'm talking about cleaning up files on your hard drive. While this is a good idea, it's not something that will affect your computer when the weather gets warmer. (and don't do the file thing too often; it's not that big of a problem these days.)
Your computer generates heat. Depending on the components, it can be a lot of heat. We're talking hot heat. The CPU, the heart of the computer, generates lots of heat. This needs to be cooled down or else it will destroy the CPU. A modern CPU running without cooling is on the short path to destruction.
Cooling for the CPU consists, in most computers, of two things: the heat sink and the fan. The heat sink is generally a lump of metal with lots of fins. The metal is used because it moves heat around very easily, balancing the heat throughout the entire lump. The finns on the heat sink are designed so that heat from the CPU flows up into them, carrying the heat away from the CPU. The fins then radiate the heat out into the air. This is where the fan kicks in. The fan moves lots and lots of air over the fins, taking away the heat. Generally, your computer will have two or three fans to move the heat from the inside of the computer to the outside, allowing cooler air back in. This moves a lot of air. This is because your computer can generate, on average, between 1400 to 2400 BTUs. An average window air conditioner will be rated at 5000 to 10,000 BTUs.
Consider that for a minute.
Now then. What happens when those cooling systems on your computer fail? What happens when the air flow around the heat sink stops of the fan ceases to work? Simple: you are in the market for a new computer.
Avoiding this is easy.
Your computer moves lots of air in through it all the time to cool itself. As with any electronic equipment, dust builds up. It's the effect of the electronic equipment itself. Even the freakiest of neat freaks cannot control dust getting into a computer. Unless you are my mother in law.
But we'll not go there.
Back on to the topic at hand. Dust. Dirt. Grime. It all build up in your computer. It builds up in the worst parts too, where the air moves the most. Through the vanes of the heat sink and on the blades of the cooling fan. Only bad things can happen in this case.
Warm weather will make it harder for your computer to cool itself. This will generally decrease the life of your expensive computer as the heat can damage the internal components.
So. How do you deal with this? Rule One: keep the vacuum cleaner away! Your vacuum will generate lots of static electricity. Forget about buying USB cleaners or their ilk. They are useless.
You may want to do this outside, as you are about to generate a lot of dust. Use some of those paper masks you can get from the hardware store.
Ideally, the cleaning should be thus:
Unplug the computer. Remove the access to the internal components. This is usually done by taking off the side panel. But not always. Figure out your case before you break something.
Ground yourself. Also ground the computer. A good anti-static wrist strap is always a good idea.
Now, when you have the access off, look. Don't touch. I've seen computers with hairballs the size of my fist. If any are present, pull them out gently. Do your best to not touch anything. If you have dust balls, think about getting it professionally done. This is where it gets nasty.
Now, using electronics grade canned air, slowly work your way down from the top to the bottom. Keep the nozzle at least six inches away from any components. Pay particular attention to the fan and heat sink. Spray the power supply from the inside of the computer outwards, as well as any other ventilation fans or openings. Do not touch any of the electronics.
If the machine is particularly dirty, you may need to pay special attention to the main fan. You'll need cotton swabs and cleaning alcohol. All of these things should be easily gotten from your local office supply store. Don't use cotton balls or Q-Tips® as they will leave lint behind. Moisten the swab with the cleaning solution (do not use rubbing alcahol) and gently rub the blades of the fan. Hold the fan blades steady while you are doing this, as they generally have delicate bearings. Do not touch any of the electronics.
Next, use a one piece towel to clean up the vents, the inside of the case cover, the inside bottom of the case and exposed cables. Again, be very careful when touching any of the insides of the computer. Do not touch any of the electronics.
Replace the cover and wipe down the exterior of the case. You have successfully cleaned your computer.
Last thing: make sure you know where your cat is. Cats always want to help clean up the computer. Getting locked in makes them upset though.
While summer is still a couple of weeks away, now is a good time to pay attention to your computer and its needs for the long hot days ahead. Many people fail to realize that their computers need a good cleaning every now and then. Some people assume that I'm talking about cleaning up files on your hard drive. While this is a good idea, it's not something that will affect your computer when the weather gets warmer. (and don't do the file thing too often; it's not that big of a problem these days.)
Your computer generates heat. Depending on the components, it can be a lot of heat. We're talking hot heat. The CPU, the heart of the computer, generates lots of heat. This needs to be cooled down or else it will destroy the CPU. A modern CPU running without cooling is on the short path to destruction.
Cooling for the CPU consists, in most computers, of two things: the heat sink and the fan. The heat sink is generally a lump of metal with lots of fins. The metal is used because it moves heat around very easily, balancing the heat throughout the entire lump. The finns on the heat sink are designed so that heat from the CPU flows up into them, carrying the heat away from the CPU. The fins then radiate the heat out into the air. This is where the fan kicks in. The fan moves lots and lots of air over the fins, taking away the heat. Generally, your computer will have two or three fans to move the heat from the inside of the computer to the outside, allowing cooler air back in. This moves a lot of air. This is because your computer can generate, on average, between 1400 to 2400 BTUs. An average window air conditioner will be rated at 5000 to 10,000 BTUs.
Consider that for a minute.
Now then. What happens when those cooling systems on your computer fail? What happens when the air flow around the heat sink stops of the fan ceases to work? Simple: you are in the market for a new computer.
Avoiding this is easy.
Your computer moves lots of air in through it all the time to cool itself. As with any electronic equipment, dust builds up. It's the effect of the electronic equipment itself. Even the freakiest of neat freaks cannot control dust getting into a computer. Unless you are my mother in law.
But we'll not go there.
Back on to the topic at hand. Dust. Dirt. Grime. It all build up in your computer. It builds up in the worst parts too, where the air moves the most. Through the vanes of the heat sink and on the blades of the cooling fan. Only bad things can happen in this case.
Warm weather will make it harder for your computer to cool itself. This will generally decrease the life of your expensive computer as the heat can damage the internal components.
So. How do you deal with this? Rule One: keep the vacuum cleaner away! Your vacuum will generate lots of static electricity. Forget about buying USB cleaners or their ilk. They are useless.
You may want to do this outside, as you are about to generate a lot of dust. Use some of those paper masks you can get from the hardware store.
Ideally, the cleaning should be thus:
Unplug the computer. Remove the access to the internal components. This is usually done by taking off the side panel. But not always. Figure out your case before you break something.
Ground yourself. Also ground the computer. A good anti-static wrist strap is always a good idea.
Now, when you have the access off, look. Don't touch. I've seen computers with hairballs the size of my fist. If any are present, pull them out gently. Do your best to not touch anything. If you have dust balls, think about getting it professionally done. This is where it gets nasty.
Now, using electronics grade canned air, slowly work your way down from the top to the bottom. Keep the nozzle at least six inches away from any components. Pay particular attention to the fan and heat sink. Spray the power supply from the inside of the computer outwards, as well as any other ventilation fans or openings. Do not touch any of the electronics.
If the machine is particularly dirty, you may need to pay special attention to the main fan. You'll need cotton swabs and cleaning alcohol. All of these things should be easily gotten from your local office supply store. Don't use cotton balls or Q-Tips® as they will leave lint behind. Moisten the swab with the cleaning solution (do not use rubbing alcahol) and gently rub the blades of the fan. Hold the fan blades steady while you are doing this, as they generally have delicate bearings. Do not touch any of the electronics.
Next, use a one piece towel to clean up the vents, the inside of the case cover, the inside bottom of the case and exposed cables. Again, be very careful when touching any of the insides of the computer. Do not touch any of the electronics.
Replace the cover and wipe down the exterior of the case. You have successfully cleaned your computer.
Last thing: make sure you know where your cat is. Cats always want to help clean up the computer. Getting locked in makes them upset though.
Labels:
clean computer,
computer,
cpu,
dirt,
dust,
dust bunnies,
heat,
heat sink
2008-04-17
Your Web Browser and You
Is it wrong for me to giggle about this?
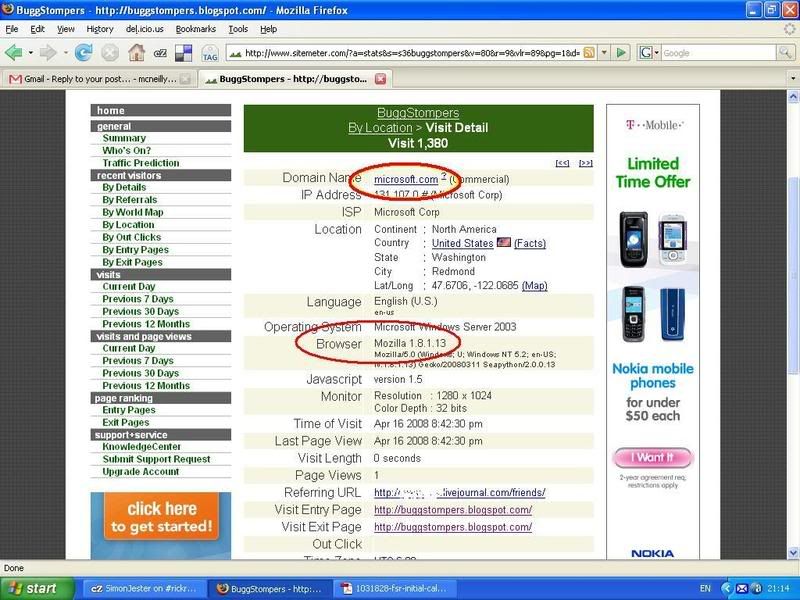
For ages now, I've told people that Mozilla Firefox is a better all around browser. It's faster, more secure and has less security vulnerabilities. The only reason I even keep it on my machines is that Microsoft has this thing where if you want to update your operating system, the only browser you can use to update is Internet Explorer. From this screen shot, it seems that even people at Microsoft think Mozilla is the better browser.

For ages now, I've told people that Mozilla Firefox is a better all around browser. It's faster, more secure and has less security vulnerabilities. The only reason I even keep it on my machines is that Microsoft has this thing where if you want to update your operating system, the only browser you can use to update is Internet Explorer. From this screen shot, it seems that even people at Microsoft think Mozilla is the better browser.
Labels:
giggle,
internet explorer,
mozilla firefox,
redmond
2008-04-01
How Your Computer Security Will Get You Arrested.
Recently one evening, I decided to spend some time engaging in the Geek sport of war driving. It's much more innocent than it sounds. War driving consists of driving around in your car with a laptop that is wireless, or 'wifi', capable. Some war drivers use special wireless antennae to look for wireless spots. If you want to know more, search for 'pringles can antenna'. Seriously.
I was using a simple Netgear wireless card on my IBM T20 Thinkpad. The computer is running Windows XP on 512M of memory. It's a cheap, reliable set up.
The term 'war driving' comes from back in the day when you had to use phone connections instead of satellite or cable. Most of the time, the computer you wanted to get access to only had one phone line. Often, you didn't know what the number of the other computer was. So, you would set up your computer to dial a range of numbers. If it hit a human or a fax machine, it would take the number off the list. If it reached another computer, it would add it to the 'good' list for you to play around with later. This aggressive search was called 'war dialing' which was coined from the Mathew Broderick 1983 movie Wargames.
War Driving comes from the idea that when you are driving around looking for these 'hot spots' you are using brute force to find wireless connections.
While driving around a light industrial area and a residential area, I came up with about 30 network connections using a program called Network Stumbler. This program is available for free on the Internet and works with most wireless cards. You start it up and let it listen for any networks in range. It will tell you what sort of connection it is, the strength, other assorted information and most importantly, if the connection has security enabled. This is a type of encryption that will only allow computers that know the encryption key to access the network. If you don't have any encryption set, anyone with a wireless capable computer can access the Internet through your network at the very least. Like the guy sitting out in his car with a laptop across the street from your house.
Okay, that's no biggie you think. So my neighbor, or anyone else with a computer with wifi, is using my network to check his mail. So what?
Well, lots of "so what". First off, he is using up your bandwidth. Bandwidth is the amount of data you can send and receive to the Internet. If your connection is slow at certain times, how do you know that your neighbor isn't downloading big files, like music or movies?
Generally, if you have a wireless connection in your home, it's via a router. The way it works is that your connection to the Internet comes in through your cable or DSL via a modem. This goes into the router and the connection is dispersed out to the various computers on your network. All the Internet provider can see is your one connection that is the router. It can't tell what or how many computers are on the other side of the router. So, your neighbor is using your bandwidth to download movies. With children.
When the FBI knocks down your door, try to convince them it wasn't you. They'll have all the proof they need to show that the end of the line was your house.
I was using a simple Netgear wireless card on my IBM T20 Thinkpad. The computer is running Windows XP on 512M of memory. It's a cheap, reliable set up.
The term 'war driving' comes from back in the day when you had to use phone connections instead of satellite or cable. Most of the time, the computer you wanted to get access to only had one phone line. Often, you didn't know what the number of the other computer was. So, you would set up your computer to dial a range of numbers. If it hit a human or a fax machine, it would take the number off the list. If it reached another computer, it would add it to the 'good' list for you to play around with later. This aggressive search was called 'war dialing' which was coined from the Mathew Broderick 1983 movie Wargames.
War Driving comes from the idea that when you are driving around looking for these 'hot spots' you are using brute force to find wireless connections.
While driving around a light industrial area and a residential area, I came up with about 30 network connections using a program called Network Stumbler. This program is available for free on the Internet and works with most wireless cards. You start it up and let it listen for any networks in range. It will tell you what sort of connection it is, the strength, other assorted information and most importantly, if the connection has security enabled. This is a type of encryption that will only allow computers that know the encryption key to access the network. If you don't have any encryption set, anyone with a wireless capable computer can access the Internet through your network at the very least. Like the guy sitting out in his car with a laptop across the street from your house.
Okay, that's no biggie you think. So my neighbor, or anyone else with a computer with wifi, is using my network to check his mail. So what?
Well, lots of "so what". First off, he is using up your bandwidth. Bandwidth is the amount of data you can send and receive to the Internet. If your connection is slow at certain times, how do you know that your neighbor isn't downloading big files, like music or movies?
Generally, if you have a wireless connection in your home, it's via a router. The way it works is that your connection to the Internet comes in through your cable or DSL via a modem. This goes into the router and the connection is dispersed out to the various computers on your network. All the Internet provider can see is your one connection that is the router. It can't tell what or how many computers are on the other side of the router. So, your neighbor is using your bandwidth to download movies. With children.
When the FBI knocks down your door, try to convince them it wasn't you. They'll have all the proof they need to show that the end of the line was your house.
2008-03-27
Remnants of Viruses
So, your anti-virus kicked ass and took names. Your computer is clean and running quickly. All is well.
Except for one small thing.
When you start up the computer, you get a couple of weird error boxes that pop up when the desktop first shows up, that look something this:
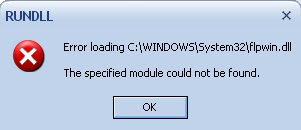
It could be any number of windows and the file and path name could be entirely different, but they will look similar to this.
No worries.
This is just the debris left over from the virus infestation. It's a dead body of the invader left on the battlefield after your side has won.
Making it go away is simple. Follow the steps below and you're pretty much guaranteed to get rid of those messages. If they continue, you've got other problems and should be dealt with accordingly. This is all about clean up though.
When your computer restarts, look for the error pop up. I'm willing to bet they won't be there.
A winner is you! Woohoo!
Except for one small thing.
When you start up the computer, you get a couple of weird error boxes that pop up when the desktop first shows up, that look something this:

It could be any number of windows and the file and path name could be entirely different, but they will look similar to this.
No worries.
This is just the debris left over from the virus infestation. It's a dead body of the invader left on the battlefield after your side has won.
Making it go away is simple. Follow the steps below and you're pretty much guaranteed to get rid of those messages. If they continue, you've got other problems and should be dealt with accordingly. This is all about clean up though.
- Click on the Start button.
- Click on the Run button.
- In the window that opens up type in "msconfig". This will bring you to the System Configuration Utility.
- On the far right, under the Startup tab, look under the Command line, scroll down and look for the specific file that is being called in the error. On the left, remove the check from the Startup Item associated with the file.
- On the bottom, click Apply, then OK.
- A pop up box will appear that asks if you want to restart the computer. You'll need to do so to have the above take place.
When your computer restarts, look for the error pop up. I'm willing to bet they won't be there.
A winner is you! Woohoo!
2008-02-06
Protection From Fraud
Con artists have been working hard to separate you from your money since the dawn of time. These days, pretending to be you and fooling banks is the con man's game and spyware is the tool of the trade. Spyware, also called malware, scumware and a host of other epithets are programs that are installed in unsuspecting computers to steal your information. Information about who you are, your name, age, income, marital status, social security number, credit card information is siphoned off and used to allow someone else to pretend to be you. You know what I mean; you've seen the commercials. Your bank, for instance, is interested in helping you protect your money from these thieves.
Or are they?
Imagine this: you go to the bank, stand in line and while you are waiting, next to you is a stand with all sorts of interesting brochures. While waiting in line, you see one brochure titled “Protect Yourself From Malware” (front, back). Oh! You like this already! You hate malware and are glad to see a bank taking an active interest in helping out their customers.
You are about to receive a shock.
Now, the shock comes in the middle section of the inside of the brochure, under the section titled “What Can I Do To Protect My Computer?”
The site www.spy-bot.net (www.safer-networking.org is the real address for Spybot) is a shadowy entity which sources say is associated with AlertSpy.com which is owned by Three W Networks Ltd., a company with a P.O. Box in Nassau. As in the phrase “off shore”. Try and find out who they are. I dare you. You might find Sasquatch too.
Anyway, this sneaky little site is a “goad site”. They goad you into thinking that something is wrong, making you panic, telling you that your system is infested with all kinds of horrible things but that they can cure you. For a fee, of course. (not to mention that they will INSTALL some of the worst spyware on your computer in the process)
They tell you about spyware removal software and list two very well known, and respected, programs designed to keep your computer spyware-free, Ad-Aware and Spybot Search and Destroy.
Many people these days have no clue to the danger they are in. Companies are often no better off. Take for example the case of Fifth Third Bancorp. Fifth Third, or 53 as they are sometimes known has $104 billion in assets, 1,181 full-service Banking Centers and branches in 12 States. They have more money than many 3rd world countries. Yet, they still can't spend enough money on making a brochure that doesn't steal your personal information.
A quick side story before we go on. One thing that the people making spyware know is that they are being hunted. Groups are hunting them down all the time. People who in their spare time, or as a full-time job track them down. Spyware creators are the ones who steal your identity. Your money is being slowly siphoned off by these criminals. One way that these predators can escape from notice for a while is to put on the clothing of one of the hunters. A wolf in sheep's clothing. For example, making a product that looks similar to the Real McCoy, say “Ad-Aware”, and using this program to INSTALL spyware onto your computer. This is what is known in the computer world as a Trojan Horse, a program that looks like it will do one thing and then do something completely different.
Now, personally, I love Spybot. It's one of my favorite anti-spyware programs. Yes, there are many anti-spyware programs and not all are alike. Some are good, some are next to useless, but that is another subject. Anyway, if you go to www.spy-bot.net and look at things, they have no association with Safer Networking, the people who make Spybot Search and Destroy, they have no connection with each other.
Spybot Search and Destroy is free to individuals. They ask for donations but you never have to pay for it. Ever.
Thus, Fifth Third is pointing you in the direction of a web site that wants to steal your name, your identity and your money. You have to pay for the privilege too. Sure, it's an innocent mistake; anyone could have done it but don't you think with $104 billion (BILLION!) in assets that they could have invested in some research, as opposed to letting the boss' nephew do it after school?
When I discovered this months ago, 53 was the first to know. That was quite a while ago and they have basically said "thanks, we'll let you know if we decide to do anything". Who knows when, or if, this behemoth of a company will fix this problem.
So, take the advice of Fifth Third and protect yourself from spyware. That you might get from Fifth Third.
Or are they?
Imagine this: you go to the bank, stand in line and while you are waiting, next to you is a stand with all sorts of interesting brochures. While waiting in line, you see one brochure titled “Protect Yourself From Malware” (front, back). Oh! You like this already! You hate malware and are glad to see a bank taking an active interest in helping out their customers.
You are about to receive a shock.
Now, the shock comes in the middle section of the inside of the brochure, under the section titled “What Can I Do To Protect My Computer?”
The site www.spy-bot.net (www.safer-networking.org is the real address for Spybot) is a shadowy entity which sources say is associated with AlertSpy.com which is owned by Three W Networks Ltd., a company with a P.O. Box in Nassau. As in the phrase “off shore”. Try and find out who they are. I dare you. You might find Sasquatch too.
Anyway, this sneaky little site is a “goad site”. They goad you into thinking that something is wrong, making you panic, telling you that your system is infested with all kinds of horrible things but that they can cure you. For a fee, of course. (not to mention that they will INSTALL some of the worst spyware on your computer in the process)
They tell you about spyware removal software and list two very well known, and respected, programs designed to keep your computer spyware-free, Ad-Aware and Spybot Search and Destroy.
Many people these days have no clue to the danger they are in. Companies are often no better off. Take for example the case of Fifth Third Bancorp. Fifth Third, or 53 as they are sometimes known has $104 billion in assets, 1,181 full-service Banking Centers and branches in 12 States. They have more money than many 3rd world countries. Yet, they still can't spend enough money on making a brochure that doesn't steal your personal information.
A quick side story before we go on. One thing that the people making spyware know is that they are being hunted. Groups are hunting them down all the time. People who in their spare time, or as a full-time job track them down. Spyware creators are the ones who steal your identity. Your money is being slowly siphoned off by these criminals. One way that these predators can escape from notice for a while is to put on the clothing of one of the hunters. A wolf in sheep's clothing. For example, making a product that looks similar to the Real McCoy, say “Ad-Aware”, and using this program to INSTALL spyware onto your computer. This is what is known in the computer world as a Trojan Horse, a program that looks like it will do one thing and then do something completely different.
Now, personally, I love Spybot. It's one of my favorite anti-spyware programs. Yes, there are many anti-spyware programs and not all are alike. Some are good, some are next to useless, but that is another subject. Anyway, if you go to www.spy-bot.net and look at things, they have no association with Safer Networking, the people who make Spybot Search and Destroy, they have no connection with each other.
Spybot Search and Destroy is free to individuals. They ask for donations but you never have to pay for it. Ever.
Thus, Fifth Third is pointing you in the direction of a web site that wants to steal your name, your identity and your money. You have to pay for the privilege too. Sure, it's an innocent mistake; anyone could have done it but don't you think with $104 billion (BILLION!) in assets that they could have invested in some research, as opposed to letting the boss' nephew do it after school?
When I discovered this months ago, 53 was the first to know. That was quite a while ago and they have basically said "thanks, we'll let you know if we decide to do anything". Who knows when, or if, this behemoth of a company will fix this problem.
So, take the advice of Fifth Third and protect yourself from spyware. That you might get from Fifth Third.
Labels:
53,
buggstompers,
fifth third,
fraud,
spyware,
virus
Subscribe to:
Posts (Atom)
