Time for spring cleaning.
While summer is still a couple of weeks away, now is a good time to pay attention to your computer and its needs for the long hot days ahead. Many people fail to realize that their computers need a good cleaning every now and then. Some people assume that I'm talking about cleaning up files on your hard drive. While this is a good idea, it's not something that will affect your computer when the weather gets warmer. (and don't do the file thing too often; it's not that big of a problem these days.)
Your computer generates heat. Depending on the components, it can be a lot of heat. We're talking hot heat. The CPU, the heart of the computer, generates lots of heat. This needs to be cooled down or else it will destroy the CPU. A modern CPU running without cooling is on the short path to destruction.
Cooling for the CPU consists, in most computers, of two things: the heat sink and the fan. The heat sink is generally a lump of metal with lots of fins. The metal is used because it moves heat around very easily, balancing the heat throughout the entire lump. The finns on the heat sink are designed so that heat from the CPU flows up into them, carrying the heat away from the CPU. The fins then radiate the heat out into the air. This is where the fan kicks in. The fan moves lots and lots of air over the fins, taking away the heat. Generally, your computer will have two or three fans to move the heat from the inside of the computer to the outside, allowing cooler air back in. This moves a lot of air. This is because your computer can generate, on average, between 1400 to 2400 BTUs. An average window air conditioner will be rated at 5000 to 10,000 BTUs.
Consider that for a minute.
Now then. What happens when those cooling systems on your computer fail? What happens when the air flow around the heat sink stops of the fan ceases to work? Simple: you are in the market for a new computer.
Avoiding this is easy.
Your computer moves lots of air in through it all the time to cool itself. As with any electronic equipment, dust builds up. It's the effect of the electronic equipment itself. Even the freakiest of neat freaks cannot control dust getting into a computer. Unless you are my mother in law.
But we'll not go there.
Back on to the topic at hand. Dust. Dirt. Grime. It all build up in your computer. It builds up in the worst parts too, where the air moves the most. Through the vanes of the heat sink and on the blades of the cooling fan. Only bad things can happen in this case.
Warm weather will make it harder for your computer to cool itself. This will generally decrease the life of your expensive computer as the heat can damage the internal components.
So. How do you deal with this? Rule One: keep the vacuum cleaner away! Your vacuum will generate lots of static electricity. Forget about buying USB cleaners or their ilk. They are useless.
You may want to do this outside, as you are about to generate a lot of dust. Use some of those paper masks you can get from the hardware store.
Ideally, the cleaning should be thus:
Unplug the computer. Remove the access to the internal components. This is usually done by taking off the side panel. But not always. Figure out your case before you break something.
Ground yourself. Also ground the computer. A good anti-static wrist strap is always a good idea.
Now, when you have the access off, look. Don't touch. I've seen computers with hairballs the size of my fist. If any are present, pull them out gently. Do your best to not touch anything. If you have dust balls, think about getting it professionally done. This is where it gets nasty.
Now, using electronics grade canned air, slowly work your way down from the top to the bottom. Keep the nozzle at least six inches away from any components. Pay particular attention to the fan and heat sink. Spray the power supply from the inside of the computer outwards, as well as any other ventilation fans or openings. Do not touch any of the electronics.
If the machine is particularly dirty, you may need to pay special attention to the main fan. You'll need cotton swabs and cleaning alcohol. All of these things should be easily gotten from your local office supply store. Don't use cotton balls or Q-Tips® as they will leave lint behind. Moisten the swab with the cleaning solution (do not use rubbing alcahol) and gently rub the blades of the fan. Hold the fan blades steady while you are doing this, as they generally have delicate bearings. Do not touch any of the electronics.
Next, use a one piece towel to clean up the vents, the inside of the case cover, the inside bottom of the case and exposed cables. Again, be very careful when touching any of the insides of the computer. Do not touch any of the electronics.
Replace the cover and wipe down the exterior of the case. You have successfully cleaned your computer.
Last thing: make sure you know where your cat is. Cats always want to help clean up the computer. Getting locked in makes them upset though.
2008-06-09
2008-04-17
Your Web Browser and You
Is it wrong for me to giggle about this?
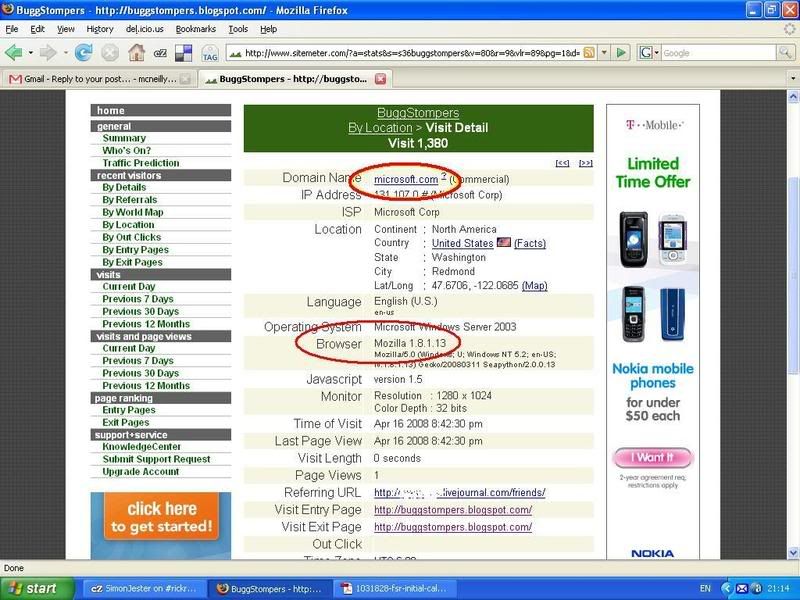
For ages now, I've told people that Mozilla Firefox is a better all around browser. It's faster, more secure and has less security vulnerabilities. The only reason I even keep it on my machines is that Microsoft has this thing where if you want to update your operating system, the only browser you can use to update is Internet Explorer. From this screen shot, it seems that even people at Microsoft think Mozilla is the better browser.

For ages now, I've told people that Mozilla Firefox is a better all around browser. It's faster, more secure and has less security vulnerabilities. The only reason I even keep it on my machines is that Microsoft has this thing where if you want to update your operating system, the only browser you can use to update is Internet Explorer. From this screen shot, it seems that even people at Microsoft think Mozilla is the better browser.
Labels:
giggle,
internet explorer,
mozilla firefox,
redmond
2008-04-01
How Your Computer Security Will Get You Arrested.
Recently one evening, I decided to spend some time engaging in the Geek sport of war driving. It's much more innocent than it sounds. War driving consists of driving around in your car with a laptop that is wireless, or 'wifi', capable. Some war drivers use special wireless antennae to look for wireless spots. If you want to know more, search for 'pringles can antenna'. Seriously.
I was using a simple Netgear wireless card on my IBM T20 Thinkpad. The computer is running Windows XP on 512M of memory. It's a cheap, reliable set up.
The term 'war driving' comes from back in the day when you had to use phone connections instead of satellite or cable. Most of the time, the computer you wanted to get access to only had one phone line. Often, you didn't know what the number of the other computer was. So, you would set up your computer to dial a range of numbers. If it hit a human or a fax machine, it would take the number off the list. If it reached another computer, it would add it to the 'good' list for you to play around with later. This aggressive search was called 'war dialing' which was coined from the Mathew Broderick 1983 movie Wargames.
War Driving comes from the idea that when you are driving around looking for these 'hot spots' you are using brute force to find wireless connections.
While driving around a light industrial area and a residential area, I came up with about 30 network connections using a program called Network Stumbler. This program is available for free on the Internet and works with most wireless cards. You start it up and let it listen for any networks in range. It will tell you what sort of connection it is, the strength, other assorted information and most importantly, if the connection has security enabled. This is a type of encryption that will only allow computers that know the encryption key to access the network. If you don't have any encryption set, anyone with a wireless capable computer can access the Internet through your network at the very least. Like the guy sitting out in his car with a laptop across the street from your house.
Okay, that's no biggie you think. So my neighbor, or anyone else with a computer with wifi, is using my network to check his mail. So what?
Well, lots of "so what". First off, he is using up your bandwidth. Bandwidth is the amount of data you can send and receive to the Internet. If your connection is slow at certain times, how do you know that your neighbor isn't downloading big files, like music or movies?
Generally, if you have a wireless connection in your home, it's via a router. The way it works is that your connection to the Internet comes in through your cable or DSL via a modem. This goes into the router and the connection is dispersed out to the various computers on your network. All the Internet provider can see is your one connection that is the router. It can't tell what or how many computers are on the other side of the router. So, your neighbor is using your bandwidth to download movies. With children.
When the FBI knocks down your door, try to convince them it wasn't you. They'll have all the proof they need to show that the end of the line was your house.
I was using a simple Netgear wireless card on my IBM T20 Thinkpad. The computer is running Windows XP on 512M of memory. It's a cheap, reliable set up.
The term 'war driving' comes from back in the day when you had to use phone connections instead of satellite or cable. Most of the time, the computer you wanted to get access to only had one phone line. Often, you didn't know what the number of the other computer was. So, you would set up your computer to dial a range of numbers. If it hit a human or a fax machine, it would take the number off the list. If it reached another computer, it would add it to the 'good' list for you to play around with later. This aggressive search was called 'war dialing' which was coined from the Mathew Broderick 1983 movie Wargames.
War Driving comes from the idea that when you are driving around looking for these 'hot spots' you are using brute force to find wireless connections.
While driving around a light industrial area and a residential area, I came up with about 30 network connections using a program called Network Stumbler. This program is available for free on the Internet and works with most wireless cards. You start it up and let it listen for any networks in range. It will tell you what sort of connection it is, the strength, other assorted information and most importantly, if the connection has security enabled. This is a type of encryption that will only allow computers that know the encryption key to access the network. If you don't have any encryption set, anyone with a wireless capable computer can access the Internet through your network at the very least. Like the guy sitting out in his car with a laptop across the street from your house.
Okay, that's no biggie you think. So my neighbor, or anyone else with a computer with wifi, is using my network to check his mail. So what?
Well, lots of "so what". First off, he is using up your bandwidth. Bandwidth is the amount of data you can send and receive to the Internet. If your connection is slow at certain times, how do you know that your neighbor isn't downloading big files, like music or movies?
Generally, if you have a wireless connection in your home, it's via a router. The way it works is that your connection to the Internet comes in through your cable or DSL via a modem. This goes into the router and the connection is dispersed out to the various computers on your network. All the Internet provider can see is your one connection that is the router. It can't tell what or how many computers are on the other side of the router. So, your neighbor is using your bandwidth to download movies. With children.
When the FBI knocks down your door, try to convince them it wasn't you. They'll have all the proof they need to show that the end of the line was your house.
2008-03-27
Remnants of Viruses
So, your anti-virus kicked ass and took names. Your computer is clean and running quickly. All is well.
Except for one small thing.
When you start up the computer, you get a couple of weird error boxes that pop up when the desktop first shows up, that look something this:
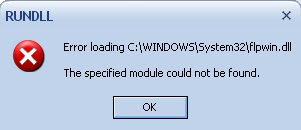
It could be any number of windows and the file and path name could be entirely different, but they will look similar to this.
No worries.
This is just the debris left over from the virus infestation. It's a dead body of the invader left on the battlefield after your side has won.
Making it go away is simple. Follow the steps below and you're pretty much guaranteed to get rid of those messages. If they continue, you've got other problems and should be dealt with accordingly. This is all about clean up though.
When your computer restarts, look for the error pop up. I'm willing to bet they won't be there.
A winner is you! Woohoo!
Except for one small thing.
When you start up the computer, you get a couple of weird error boxes that pop up when the desktop first shows up, that look something this:

It could be any number of windows and the file and path name could be entirely different, but they will look similar to this.
No worries.
This is just the debris left over from the virus infestation. It's a dead body of the invader left on the battlefield after your side has won.
Making it go away is simple. Follow the steps below and you're pretty much guaranteed to get rid of those messages. If they continue, you've got other problems and should be dealt with accordingly. This is all about clean up though.
- Click on the Start button.
- Click on the Run button.
- In the window that opens up type in "msconfig". This will bring you to the System Configuration Utility.
- On the far right, under the Startup tab, look under the Command line, scroll down and look for the specific file that is being called in the error. On the left, remove the check from the Startup Item associated with the file.
- On the bottom, click Apply, then OK.
- A pop up box will appear that asks if you want to restart the computer. You'll need to do so to have the above take place.
When your computer restarts, look for the error pop up. I'm willing to bet they won't be there.
A winner is you! Woohoo!
2008-02-06
Protection From Fraud
Con artists have been working hard to separate you from your money since the dawn of time. These days, pretending to be you and fooling banks is the con man's game and spyware is the tool of the trade. Spyware, also called malware, scumware and a host of other epithets are programs that are installed in unsuspecting computers to steal your information. Information about who you are, your name, age, income, marital status, social security number, credit card information is siphoned off and used to allow someone else to pretend to be you. You know what I mean; you've seen the commercials. Your bank, for instance, is interested in helping you protect your money from these thieves.
Or are they?
Imagine this: you go to the bank, stand in line and while you are waiting, next to you is a stand with all sorts of interesting brochures. While waiting in line, you see one brochure titled “Protect Yourself From Malware” (front, back). Oh! You like this already! You hate malware and are glad to see a bank taking an active interest in helping out their customers.
You are about to receive a shock.
Now, the shock comes in the middle section of the inside of the brochure, under the section titled “What Can I Do To Protect My Computer?”
The site www.spy-bot.net (www.safer-networking.org is the real address for Spybot) is a shadowy entity which sources say is associated with AlertSpy.com which is owned by Three W Networks Ltd., a company with a P.O. Box in Nassau. As in the phrase “off shore”. Try and find out who they are. I dare you. You might find Sasquatch too.
Anyway, this sneaky little site is a “goad site”. They goad you into thinking that something is wrong, making you panic, telling you that your system is infested with all kinds of horrible things but that they can cure you. For a fee, of course. (not to mention that they will INSTALL some of the worst spyware on your computer in the process)
They tell you about spyware removal software and list two very well known, and respected, programs designed to keep your computer spyware-free, Ad-Aware and Spybot Search and Destroy.
Many people these days have no clue to the danger they are in. Companies are often no better off. Take for example the case of Fifth Third Bancorp. Fifth Third, or 53 as they are sometimes known has $104 billion in assets, 1,181 full-service Banking Centers and branches in 12 States. They have more money than many 3rd world countries. Yet, they still can't spend enough money on making a brochure that doesn't steal your personal information.
A quick side story before we go on. One thing that the people making spyware know is that they are being hunted. Groups are hunting them down all the time. People who in their spare time, or as a full-time job track them down. Spyware creators are the ones who steal your identity. Your money is being slowly siphoned off by these criminals. One way that these predators can escape from notice for a while is to put on the clothing of one of the hunters. A wolf in sheep's clothing. For example, making a product that looks similar to the Real McCoy, say “Ad-Aware”, and using this program to INSTALL spyware onto your computer. This is what is known in the computer world as a Trojan Horse, a program that looks like it will do one thing and then do something completely different.
Now, personally, I love Spybot. It's one of my favorite anti-spyware programs. Yes, there are many anti-spyware programs and not all are alike. Some are good, some are next to useless, but that is another subject. Anyway, if you go to www.spy-bot.net and look at things, they have no association with Safer Networking, the people who make Spybot Search and Destroy, they have no connection with each other.
Spybot Search and Destroy is free to individuals. They ask for donations but you never have to pay for it. Ever.
Thus, Fifth Third is pointing you in the direction of a web site that wants to steal your name, your identity and your money. You have to pay for the privilege too. Sure, it's an innocent mistake; anyone could have done it but don't you think with $104 billion (BILLION!) in assets that they could have invested in some research, as opposed to letting the boss' nephew do it after school?
When I discovered this months ago, 53 was the first to know. That was quite a while ago and they have basically said "thanks, we'll let you know if we decide to do anything". Who knows when, or if, this behemoth of a company will fix this problem.
So, take the advice of Fifth Third and protect yourself from spyware. That you might get from Fifth Third.
Or are they?
Imagine this: you go to the bank, stand in line and while you are waiting, next to you is a stand with all sorts of interesting brochures. While waiting in line, you see one brochure titled “Protect Yourself From Malware” (front, back). Oh! You like this already! You hate malware and are glad to see a bank taking an active interest in helping out their customers.
You are about to receive a shock.
Now, the shock comes in the middle section of the inside of the brochure, under the section titled “What Can I Do To Protect My Computer?”
The site www.spy-bot.net (www.safer-networking.org is the real address for Spybot) is a shadowy entity which sources say is associated with AlertSpy.com which is owned by Three W Networks Ltd., a company with a P.O. Box in Nassau. As in the phrase “off shore”. Try and find out who they are. I dare you. You might find Sasquatch too.
Anyway, this sneaky little site is a “goad site”. They goad you into thinking that something is wrong, making you panic, telling you that your system is infested with all kinds of horrible things but that they can cure you. For a fee, of course. (not to mention that they will INSTALL some of the worst spyware on your computer in the process)
They tell you about spyware removal software and list two very well known, and respected, programs designed to keep your computer spyware-free, Ad-Aware and Spybot Search and Destroy.
Many people these days have no clue to the danger they are in. Companies are often no better off. Take for example the case of Fifth Third Bancorp. Fifth Third, or 53 as they are sometimes known has $104 billion in assets, 1,181 full-service Banking Centers and branches in 12 States. They have more money than many 3rd world countries. Yet, they still can't spend enough money on making a brochure that doesn't steal your personal information.
A quick side story before we go on. One thing that the people making spyware know is that they are being hunted. Groups are hunting them down all the time. People who in their spare time, or as a full-time job track them down. Spyware creators are the ones who steal your identity. Your money is being slowly siphoned off by these criminals. One way that these predators can escape from notice for a while is to put on the clothing of one of the hunters. A wolf in sheep's clothing. For example, making a product that looks similar to the Real McCoy, say “Ad-Aware”, and using this program to INSTALL spyware onto your computer. This is what is known in the computer world as a Trojan Horse, a program that looks like it will do one thing and then do something completely different.
Now, personally, I love Spybot. It's one of my favorite anti-spyware programs. Yes, there are many anti-spyware programs and not all are alike. Some are good, some are next to useless, but that is another subject. Anyway, if you go to www.spy-bot.net and look at things, they have no association with Safer Networking, the people who make Spybot Search and Destroy, they have no connection with each other.
Spybot Search and Destroy is free to individuals. They ask for donations but you never have to pay for it. Ever.
Thus, Fifth Third is pointing you in the direction of a web site that wants to steal your name, your identity and your money. You have to pay for the privilege too. Sure, it's an innocent mistake; anyone could have done it but don't you think with $104 billion (BILLION!) in assets that they could have invested in some research, as opposed to letting the boss' nephew do it after school?
When I discovered this months ago, 53 was the first to know. That was quite a while ago and they have basically said "thanks, we'll let you know if we decide to do anything". Who knows when, or if, this behemoth of a company will fix this problem.
So, take the advice of Fifth Third and protect yourself from spyware. That you might get from Fifth Third.
Labels:
53,
buggstompers,
fifth third,
fraud,
spyware,
virus
2008-01-28
The Difference Between a Virus and Spyware
What is the difference between a computer virus and spyware?
Okay, I like to work with analogies, so look at it this way. Spyware and viruses (or virii) are two different beasties. Sometimes they blur the lines between each other, but generally it's a case of apples and oranges.
Take for example: Spyware is like your sleazy uncle. He wheedles himself into your house, eats your food, fouls up the plumbing and staggers in a 3 AM with a couple of his drunken buddies. Stuff will disappear from your house, but nothing really big. The change jar in your kitchen will slowly dwindle down and you'll get phone calls from salesmen that your sleazy uncle told to call you. Sure, your sleazy uncle says, you'd LOVE to buy a diesel grease powered recliner chair!
He's annoying, he tells people stuff about you that you don't want them to know, he uses your stuff and makes your life much more annoying, but that's about it.
Viruses on the other hand, are like a band of angry, hungry Vikings. A virus will bust in, with horned helmets, rob you blind, destroy your stuff, hurt you in ways you didn't know possible, use your house as a base of operations to launch attacks against your friends and neighbors, then in the last action of pure spite, burn down your house in a blazing night time pyre.
Compared to a virus, spyware is a bastion of morality and goodness.
Now don't me wrong. Spyware can bring in other malicious programs, who bring in worse programs until you wake up one morning and find that what started with your sleazy uncle has wound up with you walking into the bathroom and finding some guy named Hrothgar using your toothbrush. When one domino falls, the rest are sure to follow.
Now, as to the nature of the two beasties.
First, are you protected? Sure! You proclaim. I've got $AntiVirus Product X! I'm safe. Three words: no you ain't. First off, $AntiVirus Product X is designed to protect you against viruses. Spyware, your sleazy uncle, has more plaque built up than the guy who taste-tests the burger company's french fries. End result? Your computer is so slow it's nearly useless. And as for the $AntiVirus Product X? Sure, it was 'da bomb' last decade, but today it's something of a joke. Younger, more aggressive companies who want to be king of the hill have made $AntiVirus Product Z2008 which makes the one you have look like the old guy who used to hold the 'stop' sign for you when you walked to grade school. $AntiVirus Product Z2008 is Chuck Norris; you own Barney Fife. Do some research when buying your anti-virus. Don't just grab the one off the shelf that the dork in the black tie and the pimply face has been told by his corporate masters to push of on you, the unsuspecting public.
The way a virus scanner works goes something like this: the virus scanner has been written to recognize generalities. A computer virus has a certain 'look' to it. There are new types of viruses cropping up every now and then, but for the most part all new viruses are just variations on a theme. Your virus scanner has a rough sketch of what the virus looks like. The virus scanner company releases updates (for the love of mike: update your scanner) which make the sketch clearer and tells the scanner the likely places the virus will hide. This is one case where the axiom of “information is power” is paramount.
So, armed with this information, your virus scanner sallies forth to fight the good fight. Make sure you pick the current version of Sir Lancelot, not Don Quixote. Do some research. Read some reviews. Seriously; would you trust your life to the White Knight?
Now, as to spyware, it's an altogether different situation.
The makers of anti-spyware programs have to know EXACTLY what they are looking for. No generalities are used in the spyware business. The people that make anti-spyware stuff have many researchers, pouring over new information coming in from all corners of the globe. They then must decide if the program, and that's what spyware consists of, is malicious in intent. Your computer picks up things called cookies all the time. It's a way a website can remember who you are It's useful when you want to quickly log back in to a site you go to often. When a website uses that information for malice, such as following around the Web, that is where it can turn sleazy.
Thus, your anti-spyware software has to be updated probably even more often than you would think. New sites pop up every day and spyware purveyors are like dandelions. If you slack off just for a while, your lawn will be covered in yellow.
In the end, it comes down to prevention and vigilance. Choose a good anti-virus and a good anti-spyware. Some companies claim to make a product to cover you in all cases, but just because a company makes a great refrigerator doesn't mean they can make a good cell phone. Choose well. Follow the instructions. Be vigilant. Update.
And stay away from MySpace.
That is another story though...
Okay, I like to work with analogies, so look at it this way. Spyware and viruses (or virii) are two different beasties. Sometimes they blur the lines between each other, but generally it's a case of apples and oranges.
Take for example: Spyware is like your sleazy uncle. He wheedles himself into your house, eats your food, fouls up the plumbing and staggers in a 3 AM with a couple of his drunken buddies. Stuff will disappear from your house, but nothing really big. The change jar in your kitchen will slowly dwindle down and you'll get phone calls from salesmen that your sleazy uncle told to call you. Sure, your sleazy uncle says, you'd LOVE to buy a diesel grease powered recliner chair!
He's annoying, he tells people stuff about you that you don't want them to know, he uses your stuff and makes your life much more annoying, but that's about it.
Viruses on the other hand, are like a band of angry, hungry Vikings. A virus will bust in, with horned helmets, rob you blind, destroy your stuff, hurt you in ways you didn't know possible, use your house as a base of operations to launch attacks against your friends and neighbors, then in the last action of pure spite, burn down your house in a blazing night time pyre.
Compared to a virus, spyware is a bastion of morality and goodness.
Now don't me wrong. Spyware can bring in other malicious programs, who bring in worse programs until you wake up one morning and find that what started with your sleazy uncle has wound up with you walking into the bathroom and finding some guy named Hrothgar using your toothbrush. When one domino falls, the rest are sure to follow.
Now, as to the nature of the two beasties.
First, are you protected? Sure! You proclaim. I've got $AntiVirus Product X! I'm safe. Three words: no you ain't. First off, $AntiVirus Product X is designed to protect you against viruses. Spyware, your sleazy uncle, has more plaque built up than the guy who taste-tests the burger company's french fries. End result? Your computer is so slow it's nearly useless. And as for the $AntiVirus Product X? Sure, it was 'da bomb' last decade, but today it's something of a joke. Younger, more aggressive companies who want to be king of the hill have made $AntiVirus Product Z2008 which makes the one you have look like the old guy who used to hold the 'stop' sign for you when you walked to grade school. $AntiVirus Product Z2008 is Chuck Norris; you own Barney Fife. Do some research when buying your anti-virus. Don't just grab the one off the shelf that the dork in the black tie and the pimply face has been told by his corporate masters to push of on you, the unsuspecting public.
The way a virus scanner works goes something like this: the virus scanner has been written to recognize generalities. A computer virus has a certain 'look' to it. There are new types of viruses cropping up every now and then, but for the most part all new viruses are just variations on a theme. Your virus scanner has a rough sketch of what the virus looks like. The virus scanner company releases updates (for the love of mike: update your scanner) which make the sketch clearer and tells the scanner the likely places the virus will hide. This is one case where the axiom of “information is power” is paramount.
So, armed with this information, your virus scanner sallies forth to fight the good fight. Make sure you pick the current version of Sir Lancelot, not Don Quixote. Do some research. Read some reviews. Seriously; would you trust your life to the White Knight?
Now, as to spyware, it's an altogether different situation.
The makers of anti-spyware programs have to know EXACTLY what they are looking for. No generalities are used in the spyware business. The people that make anti-spyware stuff have many researchers, pouring over new information coming in from all corners of the globe. They then must decide if the program, and that's what spyware consists of, is malicious in intent. Your computer picks up things called cookies all the time. It's a way a website can remember who you are It's useful when you want to quickly log back in to a site you go to often. When a website uses that information for malice, such as following around the Web, that is where it can turn sleazy.
Thus, your anti-spyware software has to be updated probably even more often than you would think. New sites pop up every day and spyware purveyors are like dandelions. If you slack off just for a while, your lawn will be covered in yellow.
In the end, it comes down to prevention and vigilance. Choose a good anti-virus and a good anti-spyware. Some companies claim to make a product to cover you in all cases, but just because a company makes a great refrigerator doesn't mean they can make a good cell phone. Choose well. Follow the instructions. Be vigilant. Update.
And stay away from MySpace.
That is another story though...
2008-01-24
Did You Back Up Your Files Today?
Backing up your files can be a pain. Can your business afford to lose $2.5 million though?
Disgruntled Employee Accused of Deleting $2.5 Million Worth of Files
Disgruntled employee sees an add in the local paper describing what she thought sounded like her job. So, in a pre-emptive action, she goes into the off and click, click, clicks away several years of architectural drawings.
Turns out the job listing wasn't to replace her.
At least at that point, it wasn't.
This get's down to backing up. The company that she decided to get 'revenge' on, Steven E. Hutchins Architects, made several mistakes. It doesn't take an angry employee to wipe out important files. Equipment failure, fires, burglars or a good old tornado are a fraction of the myriad of things to threaten your important computer files.
You have your files all neatly stored away on your hard drive? We in the computer repair industry say there are two types of hard drive; those that have failed and those that have not yet failed. You might get lucky and have your computer's hard drive last until you get a whole new system, just don't bet on it. Murphy is always waiting in the dark corners looking for a place to happen.
As is mentioned in the article, the files were able to be recovered. Quite often, this is not an easy thing. This was just about deletion of the files from the disk. The way a file is deleted from your hard drive is strikingly simple: you take part of the name of the file away. The computer then assumes that the space where the file is can now be used for other things. It will then happily write other, newer files on top of the space. The first level of data recovery comes with trying to get those names back before the computer writes something on top of the old files. Time is of the essence in these cases. If you have accidentally deleted something, do nothing else. Nothing! Step away from the computer and call for help.
Depending on the severity of the data loss, these retrievals can cost you at the very least hundreds of dollars. More severe loss, such as physical destruction of your hard drive can run into thousands of dollars. This type of recovery involves sending your hard drive to far off places where people in paper suits and filter masks perform delicate operations in facilities cleaner than hospitals.
Don't let this happen. Learn how to back up your data. Preferably in more than one place. This can be done in several fashions, such as burning all your important files to disk, or using online storage where guys in too-tight shirts drink Dew all night and ensure your data is well cared for. The benfit of paying for a service like this is, if they screw up, the chances of them losing your data is slim, but if they do, they carry insurance. And you can take away their bag of Cheetos too.
Disgruntled Employee Accused of Deleting $2.5 Million Worth of Files
Disgruntled employee sees an add in the local paper describing what she thought sounded like her job. So, in a pre-emptive action, she goes into the off and click, click, clicks away several years of architectural drawings.
Turns out the job listing wasn't to replace her.
At least at that point, it wasn't.
This get's down to backing up. The company that she decided to get 'revenge' on, Steven E. Hutchins Architects, made several mistakes. It doesn't take an angry employee to wipe out important files. Equipment failure, fires, burglars or a good old tornado are a fraction of the myriad of things to threaten your important computer files.
You have your files all neatly stored away on your hard drive? We in the computer repair industry say there are two types of hard drive; those that have failed and those that have not yet failed. You might get lucky and have your computer's hard drive last until you get a whole new system, just don't bet on it. Murphy is always waiting in the dark corners looking for a place to happen.
As is mentioned in the article, the files were able to be recovered. Quite often, this is not an easy thing. This was just about deletion of the files from the disk. The way a file is deleted from your hard drive is strikingly simple: you take part of the name of the file away. The computer then assumes that the space where the file is can now be used for other things. It will then happily write other, newer files on top of the space. The first level of data recovery comes with trying to get those names back before the computer writes something on top of the old files. Time is of the essence in these cases. If you have accidentally deleted something, do nothing else. Nothing! Step away from the computer and call for help.
Depending on the severity of the data loss, these retrievals can cost you at the very least hundreds of dollars. More severe loss, such as physical destruction of your hard drive can run into thousands of dollars. This type of recovery involves sending your hard drive to far off places where people in paper suits and filter masks perform delicate operations in facilities cleaner than hospitals.
Don't let this happen. Learn how to back up your data. Preferably in more than one place. This can be done in several fashions, such as burning all your important files to disk, or using online storage where guys in too-tight shirts drink Dew all night and ensure your data is well cared for. The benfit of paying for a service like this is, if they screw up, the chances of them losing your data is slim, but if they do, they carry insurance. And you can take away their bag of Cheetos too.
2008-01-23
Greetings!
Welcome to the BuggStompers blog. We're glad you've stopped by to see what we're all about. This blog is for you, the customers. We want to show you a bit of the personal side of BuggStompers: our staff, our philosophy, our hopes and dreams. Well, maybe not that personal.
Feel free to comment as you wish, tell us how we're doing, or just drop a friendly note.
And remember, if it has to do with computers, we can fix it!
Feel free to comment as you wish, tell us how we're doing, or just drop a friendly note.
And remember, if it has to do with computers, we can fix it!
Subscribe to:
Posts (Atom)
